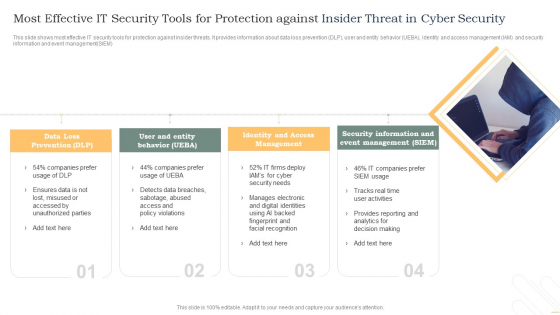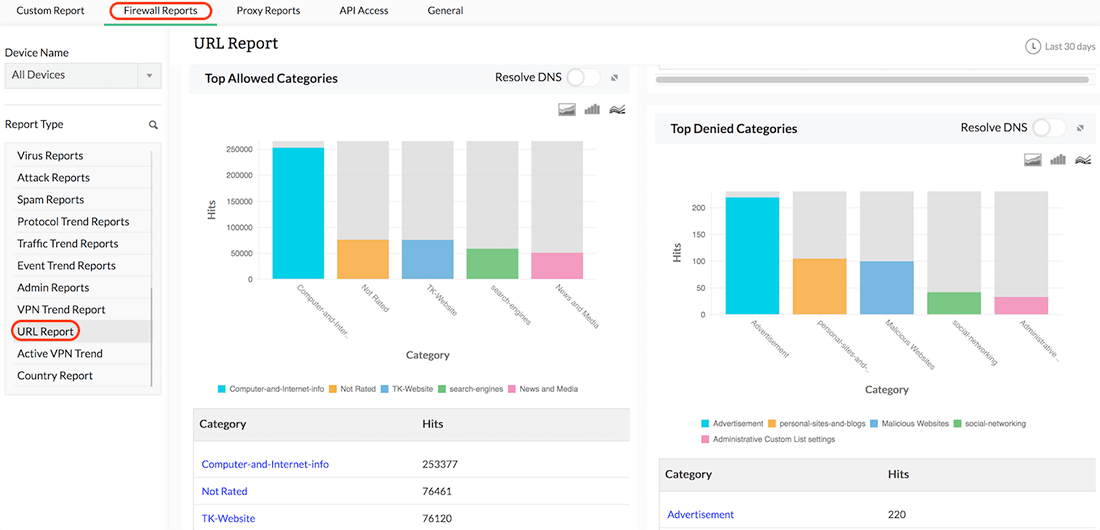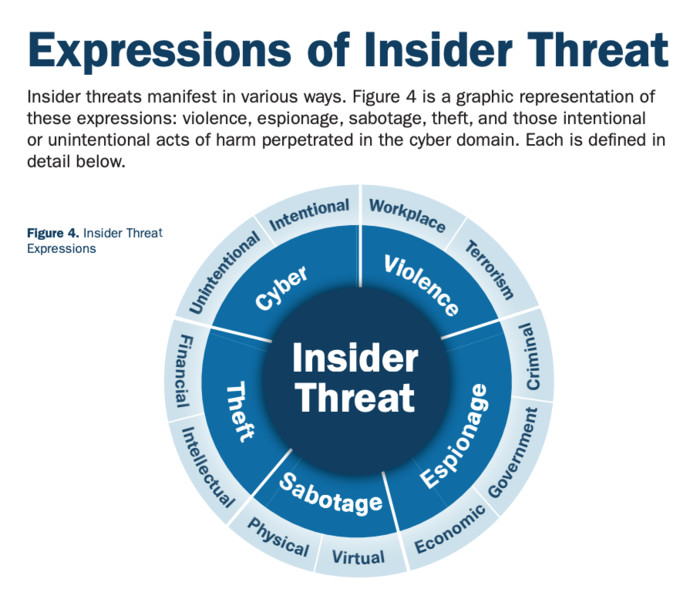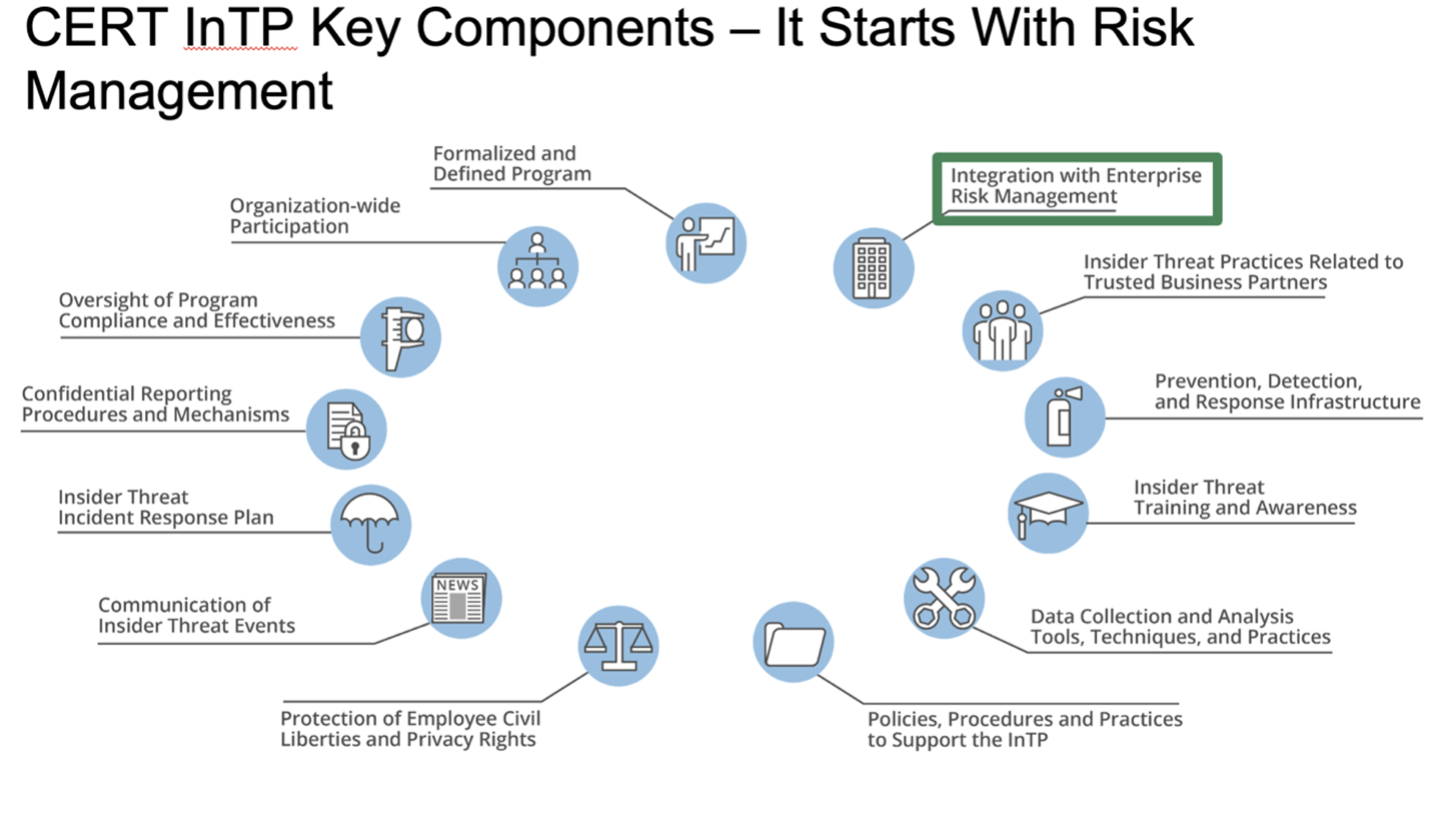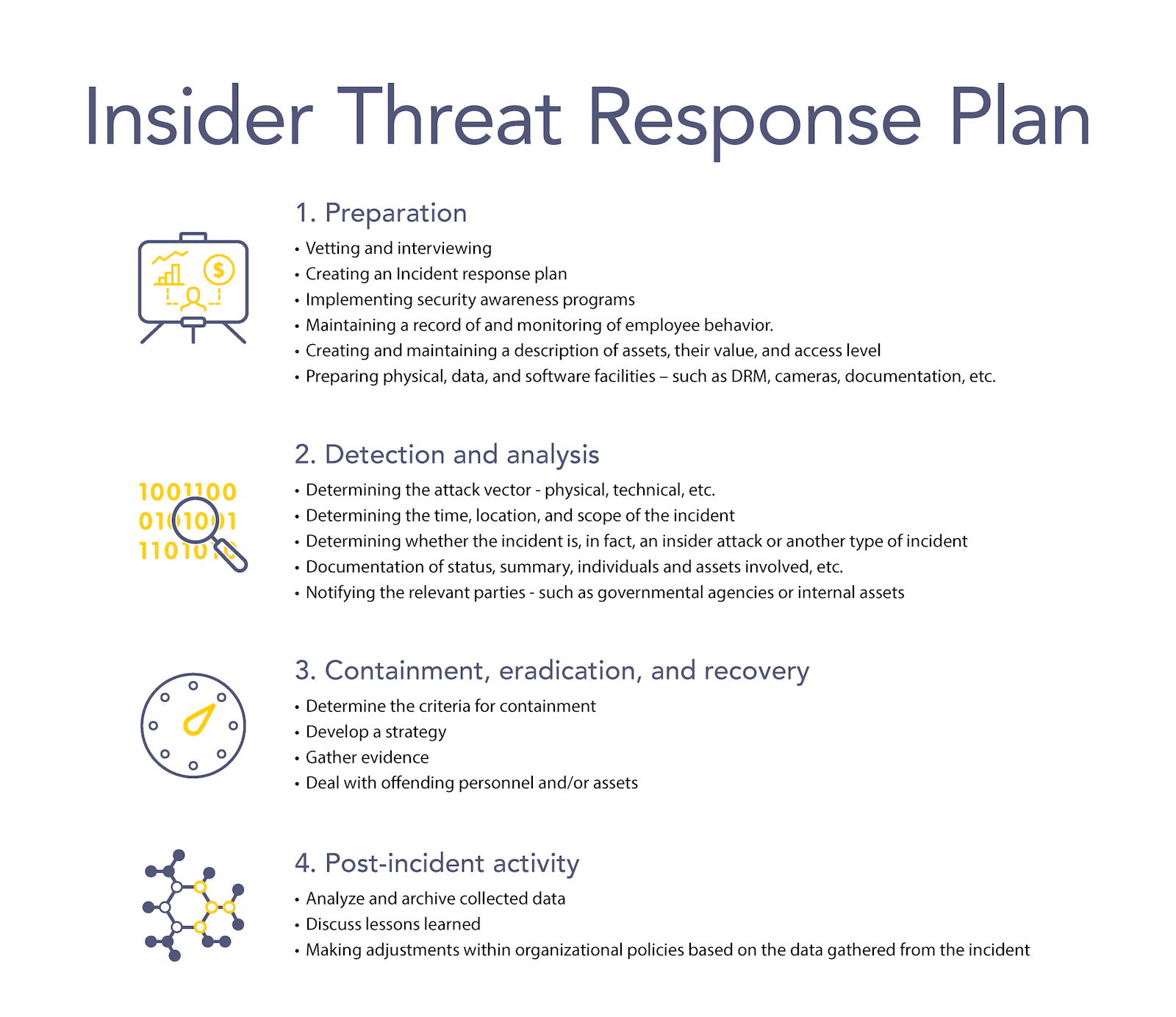
Insider Threat Detection Tools Ppt Powerpoint Presentation Layouts Graphic Tips Cpb | PowerPoint Slides Diagrams | Themes for PPT | Presentations Graphic Ideas

Understanding and Managing Insider Threats in Cybersecurity – Reveal Risk – Cybersecurity Consulting and Services