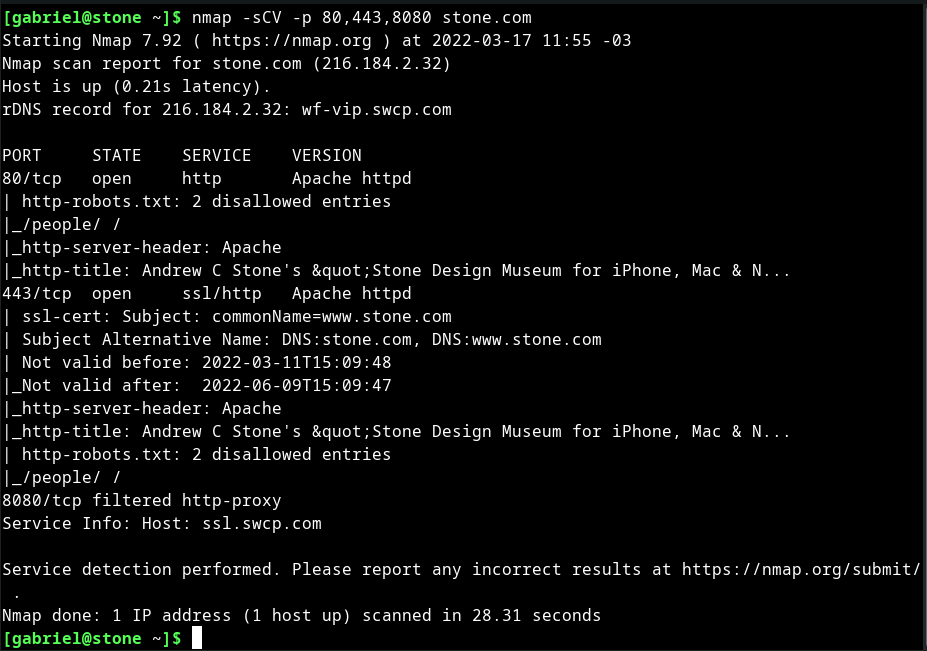
Web Application Enumeration. The enumeration phase is the first (and… | by Gabriel V. Mendes | stolabs | Medium
GitHub - saleem8054/web-enumeration-tool: This tool is for bug bounty hunters. This script will complete your first step of hacking automatically which is Reconnaissance.
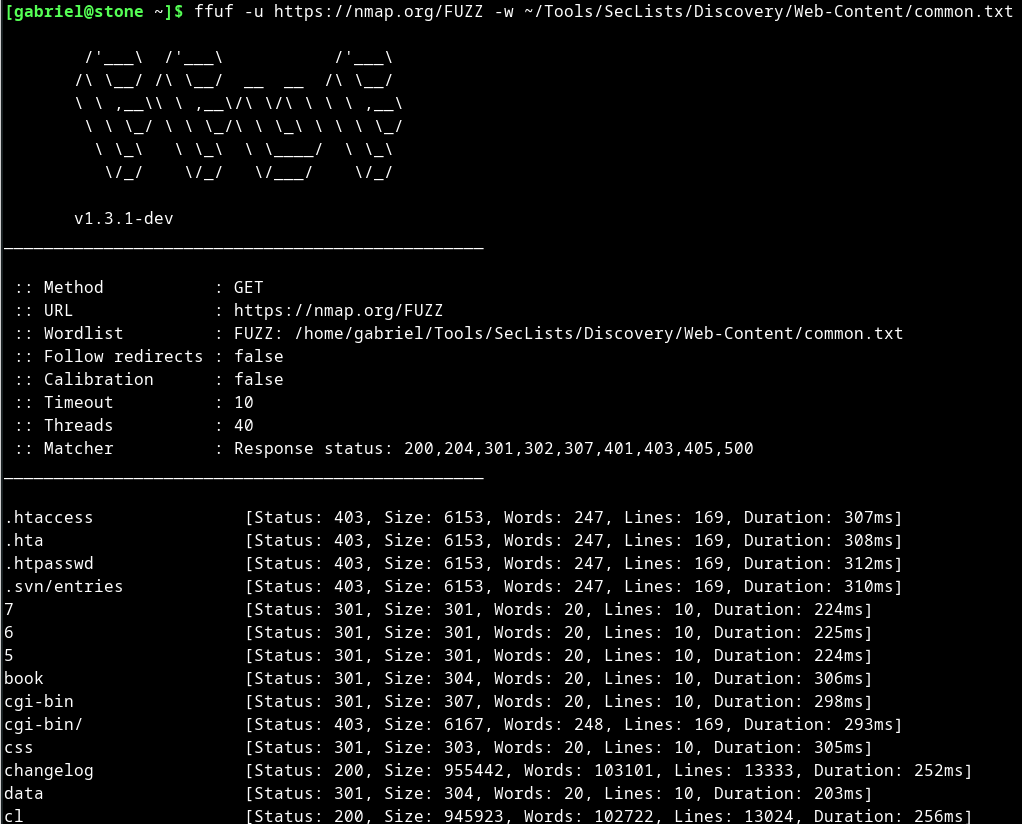
Web Application Enumeration. The enumeration phase is the first (and… | by Gabriel V. Mendes | stolabs | Medium





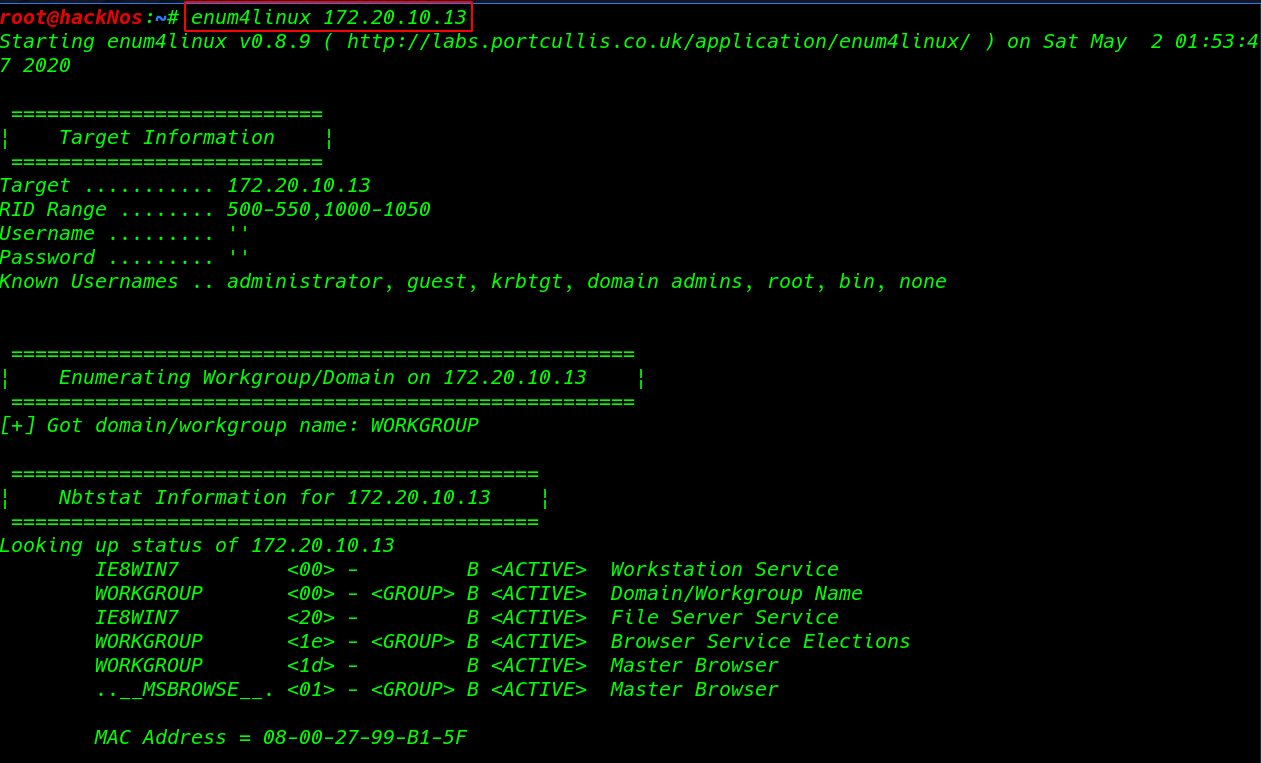
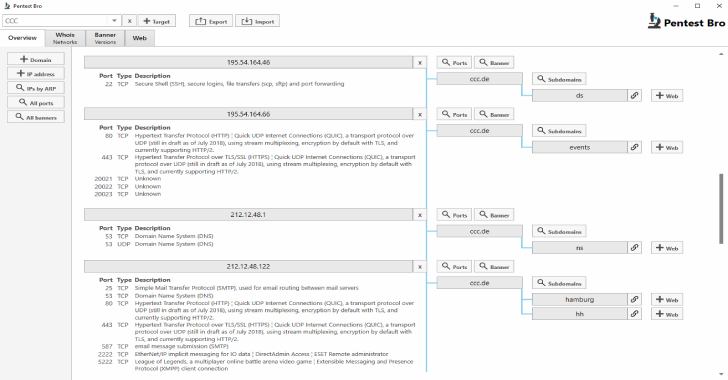







![Top 5 Subdomain Enumeration Tools [Web Application Pentest] | GoLinuxCloud Top 5 Subdomain Enumeration Tools [Web Application Pentest] | GoLinuxCloud](https://www.golinuxcloud.com/wp-content/uploads/subfinder-1.png)

![Top 5 Subdomain Enumeration Tools [Web Application Pentest] | GoLinuxCloud Top 5 Subdomain Enumeration Tools [Web Application Pentest] | GoLinuxCloud](https://www.golinuxcloud.com/wp-content/uploads/puredns.png)